CSCI 107 -- Browser Privacy
Secure pages
Let's start by opening up a second browser window
and then loading page https://www.cs.unca.edu.
Notice that the URL starts with https: rather than
http: . The additional 's' is for secure.
Look at the bottom our this new browser window. You should see
a little lock  .
If you place your mouse over the lock, the browser should proclaim
SSL Secured (128 bit).
Now double-click on the lock. This should display some information
about the certificate for the www.cs.unca.edu
web site.
.
If you place your mouse over the lock, the browser should proclaim
SSL Secured (128 bit).
Now double-click on the lock. This should display some information
about the certificate for the www.cs.unca.edu
web site.
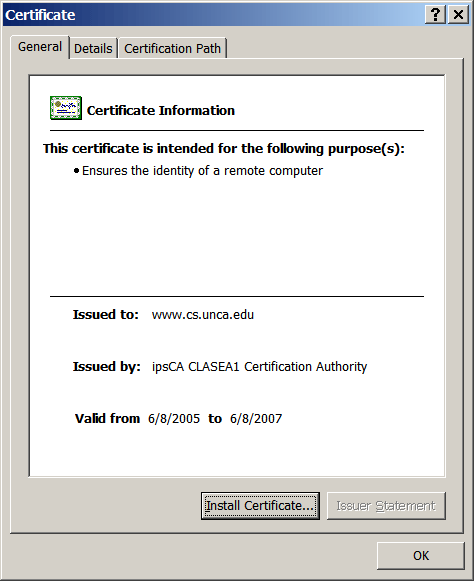
We're going to take a little while now to look at this certificate,
and then we're going to explain a bit more about it.
Select the Details tab
within the Certificate window
and scroll bar to look at some of the fields associated with the
certificate.
Every certificate must have a public key.
Double-click the field labeled Public key
to display the key for this certificate.
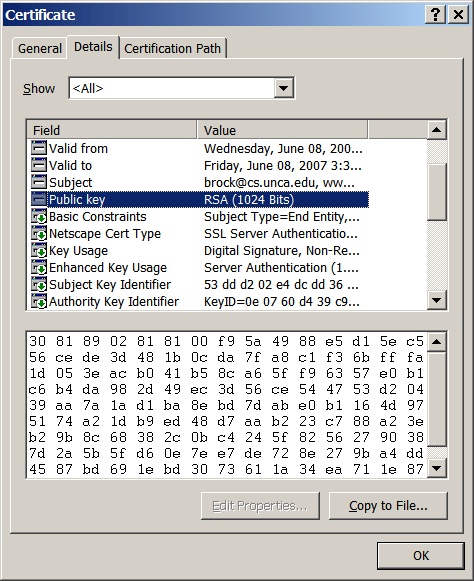
In this case the key is 1024 bits long.
No other key in the universe should have this same value.
Now go to the remaining tab,
Certification Path.
This will give you information about the
certification authority that validates the
www.cs.unca.edu web site.
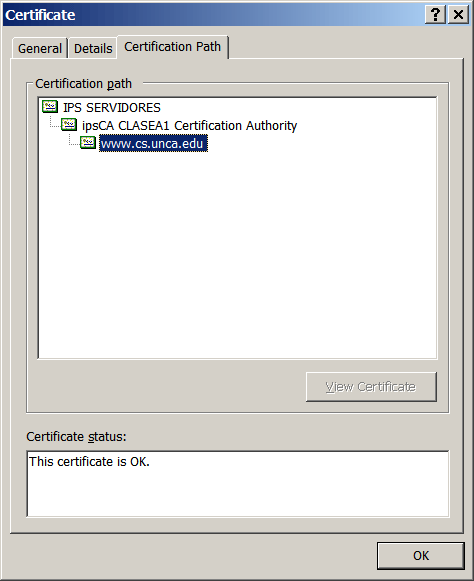
Our certification authority is
IPS Certification Authority, S.L.,
which is located in Barcelona. Why did we get our certificate
from a Spanish company? Because it's free for educational institutions!
Public Key Encryption
Public key encryption has been around for almost three decades.
The best-known company in the field is
RSA Security.
"RSA" is the initials of Rivest, Shamir, and Adleman,
the designers of an early public key algorithm.
The algorithm uses prime numbers to send secret messages.
More information about the mathematics involved can be
found at the Wikipeida
entry for RSA.
As long as you ignore the math, the basic idea isn't so complicated.
Let's say that Mr. CIA
wants to receive secret messages.
Mr. CIA uses all that RSA
mathematics to generate two keys: a public and a private.
The public key is given out to the entire world.
The private key is kept secret.
When you want to send Mr. CIA a secret message, you look up
his public key. Remember, it's available to the entire world.
The next steps are magic. You use his public key to
encrypt your message. Only the possessor of the
private key, that is, Mr. CIA, can decrypt the message.
That's the real magic!
Before Mr. CIA can send you a secret message, you
must generate your own public and private keys.
Then Mr. CIA encrypt the secret message with your
public key and only you can read it.
It gets even better! If Mr. CIA encrypts
a message with his private key, then you
can decrypt it with his public key.
But only Mr. CIA knows his private key, so
we can be sure that this message came only from Mr. CIA.
Now back to https://www.cs.unca.edu .
This computer has its own public key. You saw it just
a moment ago. If it encrypts some data with its private
key, then your browser knows it's really
talking to www.cs.unca.edu.
The real story is complicated and explained at the
Wikipedia
entry for transport layer security.
The short, and fairly accurate,
summary is that www.cs.unca.edu chooses
a session key to be used for its confidential data interchanges
with your browser. It then uses its public key to send the
session key to your browser and now your browser and
www.cs.unca.edu can have a secret exchange.
Hopefully, you now understand a bit about how www.cs.unca.edu
and your browser uses a public key.
Certification Authorities
But how do we know which public key really belongs to
www.cs.unca.edu? That's where the
certification authorities make their money.
The certification authorities validate the public key.
So, who validates the certification authorities.
Well, your browser comes with some pre-loaded
certification authorities.
Go to your other browser window and go through
the menu selections:
Tools ⇒
Internet Options...
which brings up a window labeled
Internet Options.
Next select the Content tab
and finally press on the box labeled
Certificates... which is
in the middle of the window.
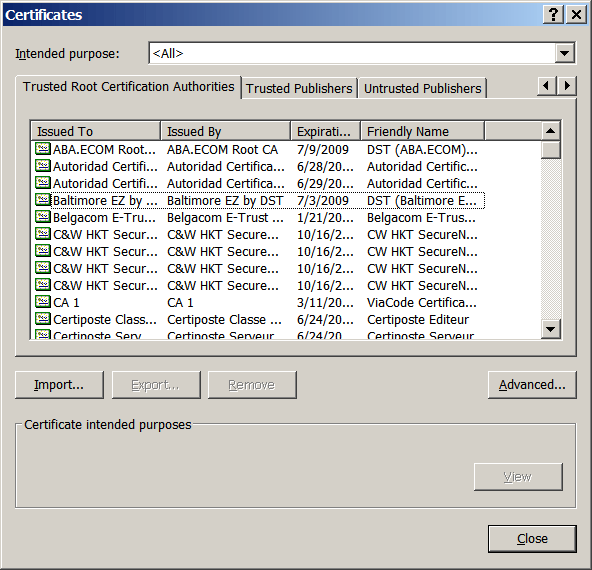
Then you can select the tab labeled
Trusted Root Certification Authorities
to see Internet Explorer's built-in list of trusted authorities.
The Uncertified
Sometimes you will encounter uncertified or expired sites.
One of these is Walt's World which is the world
of an illustrious UNCA faculty members and appears at the URL
http://www.waltsworld.us.
Go ahead and connect to http://www.waltsworld.us and you'll receive a "security alert" from
the browser.
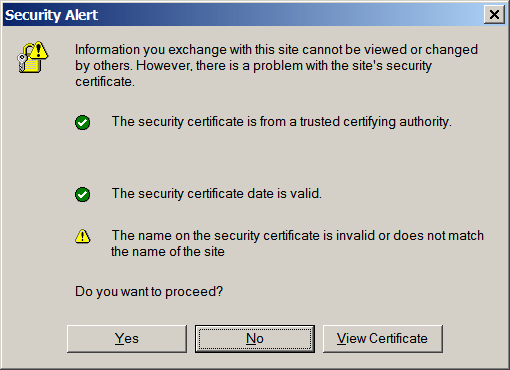
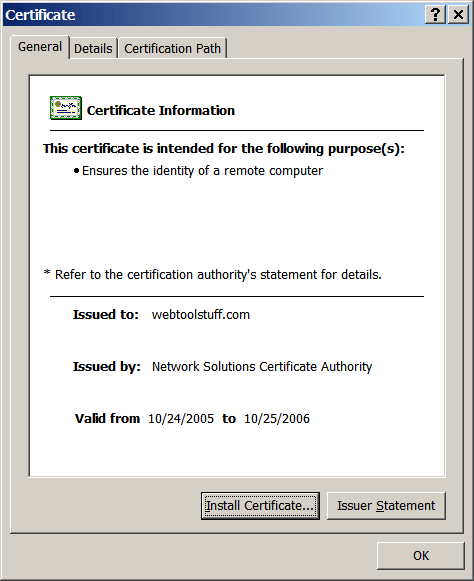
If you click the View Certificate button, you'll see that the
certificate used at www.waltsworld.us was actually
issued to webtoolstuff.com. Browsers may not approve
of this, but sometimes a professor must be creative.
Your part
In this lab, you're going to answer a few question and
turn them in to the instructor.
Your part: Looking up a certificate
Find out the name of the company that has issued a
cerficate to the www.unca.edu web site
along with the first four digits of the public key for
the www.unca.edu web site.
Remember to connect to https://www.unca.edu to answer this
question.
Your part: Looking up a certificate authorities
What is the official name of one of the root certification authorities
of the Equifax credit report company?
Your part: Obtaining a key
Let's take a little while to generate a private key.
This one won't work for a secure web site, but it would be
good enough for Secure Shell (SSH) login and file transfer.
Begin by starting the program PuTTYgen.
In KH037, you'll find this program from the start
button as follows:
start ⇒
Department Applications ⇒
CSCI ⇒
WinSCP3 ⇒
PuTTYgen.
After you see the initial
PuTTY Key Generator
window, press the Generate button.
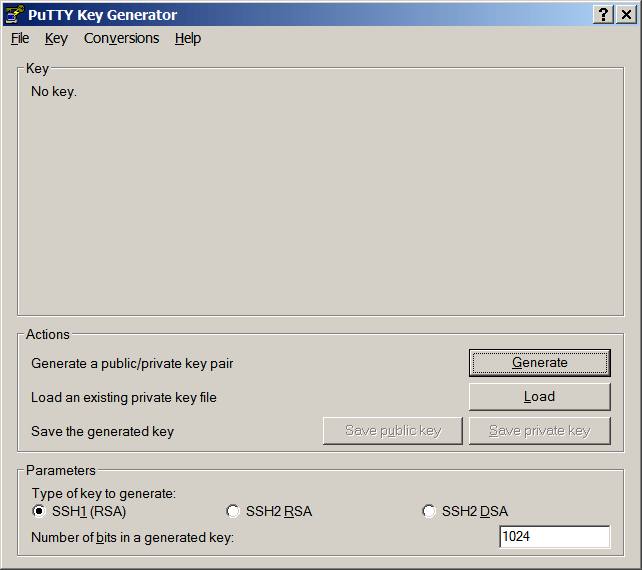
Next you must wiggle your mouse in the blank area. Your random
mouse gyrations will be used to generate a random public key.
Web sites also use randomly generated keys, but they aren't
as much fun to generate.
When you have a key, show it to your instructor.
Cookies
Web sites use cookies to collect information about you.
Originally cookies were intended for use in Internet "shopping
carts", but today web sites use them for other purposes, such as
saving visitor "preferences" or simply to collect statistics about
the viewing habits of web users.
Every cookie has a name, like "user_id", and a value,
like "XR15x67yZ". When you connect to a web site, it may ask your
browser to remember a cookie. When you connect to the web site, or perhaps
some related web sites, in the future; your browser will reveal this
cookie to the web server.
Cleaning out the cookies
Let's start by looking at your present cookies.
On Internet Explorer, use the menu sequence
Tools ⇒
Internet Options...
bring up the Internet Options
window. While the General tab
is selected, press the button labeled
Settings...
which is in the little box labeled
Temporary Internet files.
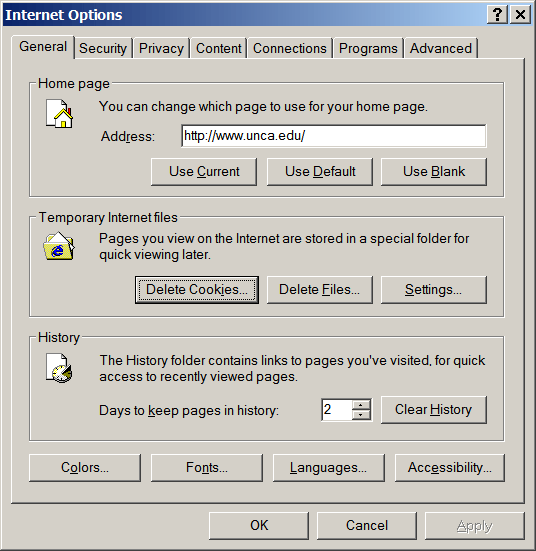
This will raise a window labeled simply
Settings. Now press the
View Files... button.
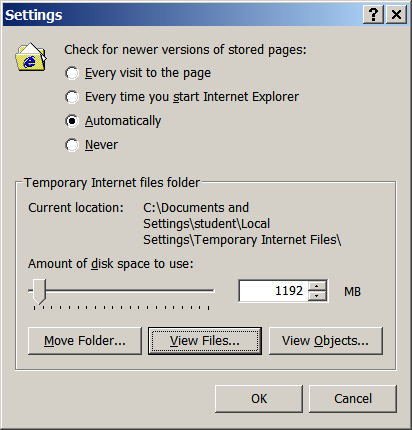
At this point, you'll see some of the information the browser
is "remembering" about you. Some of these entries may
be cookies. Others will be cached copies
of web pages and images you have viewed in the past.
Let's get rid of all this "temporary" Internet information
so that we can start the remainder of this lab with a clean slate.
Go ahead and close the
Temporary Internet Files
and Settings windows. However,
remember how you got to them.
When you get back to the
Internet Options window,
press both the
Delete Cookiies... and
Delete Files... button to erase evidence of your past activities.
When you see the Delete Files window,
be sure to check the box to delete all offline content.
Getting a cookie
Let's install a cookie.
All you have to do is press the following link
to visit the page cookie.cgi.
The cgi in the page name is an abbreviation
for common gateway interface. A cgi page is generated
by calling a program that create some HTML.
Read the page generated by cookie.cgi and then close it
and return to the point in the lab.
Glad to have you back on board.
Remember how you got to that
Temporary Internet Files
just a few minutes ago. Now return to it and see if you
can find your cookie. You should see some entries like
those shown below:
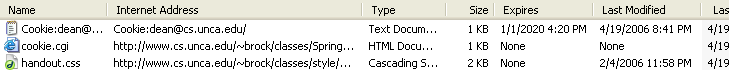
You can double-click on the entry that starts with
Cookie: and Internet Explorer will give you
a rather boring display of the cookie's contents.
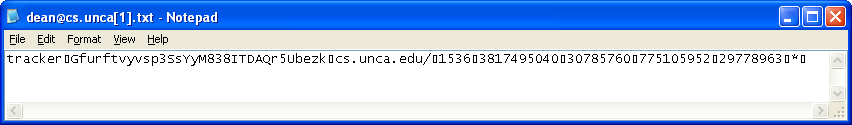
In this situation, Mozilla Firefox provides a much better view.
Just for fun view
the cookie injector page
a second time. Read it, close it, and go on.
Getting a batch of cookies
Now let's press a link to visit a well-know web site,
www.microsoft.com.
Don't tarry. There's more to do here.
Now take another look at your
Temporary Internet Files.
This time, you'll see cookies not only from microsoft.com,
but also from other sites such as webtrendslive.com.
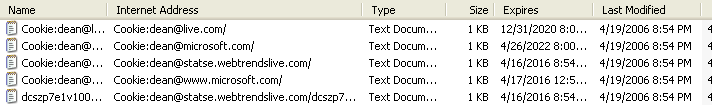
When you visit a site in one domain, such as microsoft.com,
and are rewarded with a cookie from another domain,
such as webtrendslive.com; this cookie is
called a third party cookie.
Third party cookies are usually installed by web pages
containing Javascript code or web bugs, itsy bitsy
GIF images.
Third party cookies are somewhat controversial.
In general, they enable information regarding
your web browsing activities at many different sites to
be collected in one place, and then possibly shared.
For example, a car insurance company might like to generate
a special web page with increased rates for those who have
previously visited the web site for HOT ROD magazine.
However in practice, third party cookies are far more innocuous.
Generally, they are used to audit marketing claims or verify
"hit" rates. Nonetheless, most web browsers do allow you
to "block" most, of not all, third-party cookies. In Internet Explorer,
you can do this by going to the
Internet Options window
and then pressing the
Privacy tab.
Your part: Finding cookies
Visit the web site
www.macromedia.com
and see what third party cookie will be installed by Macromedia.
Take the internet address for this third copy, stick www for
it, and visit the web site for the company that installed the third
party. [Hint: It will look something like www.207.net .]
Connect to the WWW site for this company and then read a bit of
its privacy policy. Search for the term and write down the name
of a two web phrase that is a synonym for clear gif.
[Hint: The first word is "web".]
E-mail
We all know about those
Nigerian email scams
and those phishing messages that seek
private information about your bank accounts.
However, there are email messages that try to figure out
a bit more about you. For example, take a look at
a HTML file
containing a harmless message.
Now, right click on the picture and
select Properties from the bottom
of the pop-up menu.
A Properties window will be displayed.
Notice that the name associated with the JPEG image is
cscifac.jpg?B007X2006XX.
What's the purpose of the B007X2006XX after the question mark?
In this case nothing. However if you receive an HTML message with
an image reference like
http://www.spamiam.xyz/cscifac.jpg?B007X2006XX, your email
reader might send a request back to www.spamiam.xyz
for the file cscifac.jpg?B007X2006XX.
It could be that the B007X2006XX is a special key that
is only included in messages sent to your email address.
The folks at www.spamiam.xyz would then know:
(1), they have a valid email address in their database,
and (2), someone really is reading email at that address.
Your part: The properties
Show your instructor your Properties window,
turn in your sheet with the certificate information,
finish those overdue assignments,
and go study for your final exams.
 .
If you place your mouse over the lock, the browser should proclaim
SSL Secured (128 bit).
Now double-click on the lock. This should display some information
about the certificate for the www.cs.unca.edu
web site.
.
If you place your mouse over the lock, the browser should proclaim
SSL Secured (128 bit).
Now double-click on the lock. This should display some information
about the certificate for the www.cs.unca.edu
web site.












