SSH (Secure Shell) is becoming a widely used method for transfering files and remote login. Many universities have even banned all remote file transfer except those using SSH. The Department of Computer Science at UNCA also requires SSH for its transfer.
Most people use the "open" implementations of SSH. Linux users generally use the OpenSSH tools, and Windows users use PuTTY for remote login and SSH-aware FTP programs, such as WinSCP, for file transfer.
SSH is pretty simple to use. In it most common usage, a remote file server generates a public key that is held by client programs, such as home PC's. On the first connection to the server, the home PC is asked to accept the remote key in an exchange similar to the following:
The authenticity of host 'candler.cs.unca.edu (152.18.69.33)' can't be established. RSA key fingerprint is c5:a5:92:94:6c:e1:9b:7d:cb:4d:a1:6e:24:00:45:37. Are you sure you want to continue connecting (yes/no)?
Once a key is accepted, all communication between the home PC and the server is encrypted. This makes it possible to transmit passwords to the remote server without fear that those passwords will be intercepted and used maliciously.
Go ahead and start up PuTTY and use it to connect to UNCA's mail server for its students. That computer is bulldog.unca.edu. All you have to do it type the name of computer in the Host Name box.
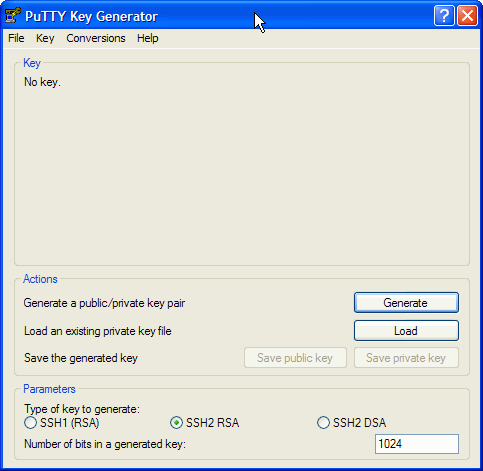
It's also possible to generate your own public/private key pair for
use with SSH. Start the program PuTTYgen and
then press the Generate button.

Now's the (only) fun part. Move your mouse around in the box
to generate a random key for SSH.
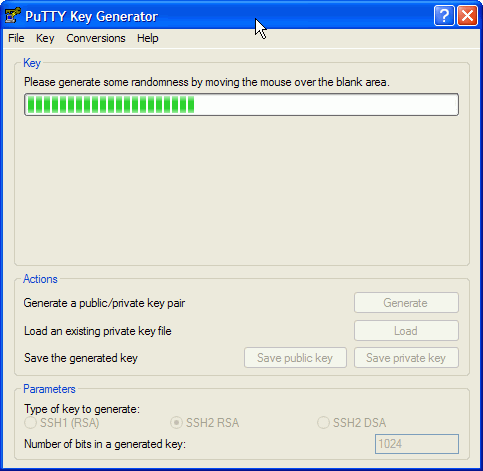
Soon you'll have your own random key.
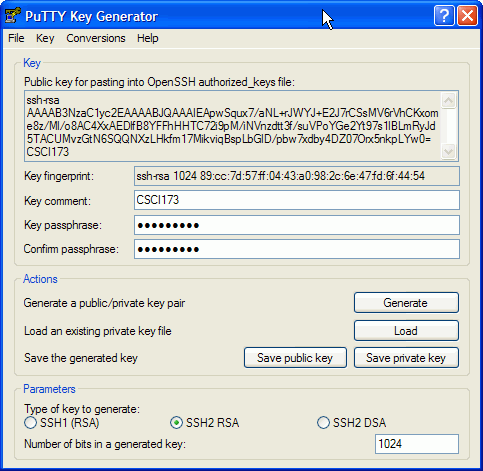
Use the Key comment: field to give your key
a useful name and use the Key passphrase: to specify
a key to unlock your password. By locking your
password with these phrase, you make sure that the person
who steals your home PC won't be able to also use your
private key.
Next save your private and public keys. Remember, the private
key is protected by your passphrase.
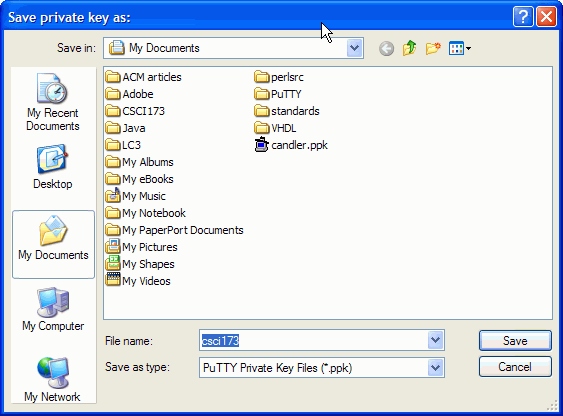
You might also want to look at your public key. It's just a sequence of strange letters.
---- BEGIN SSH2 PUBLIC KEY ---- Comment: "CSCI173" AAAAB3NzaC1yc2EAAAABJQAAAIEApwSqux7/aNL+rJWYJ+E2J7rCSsMV6rVhCKxo me8z/Ml/o8AC4XxAEDlfB8YFFhHHTC72i9pM/iNVnzdtt3f/suVPoYGe2Yt97s1l BLmRyJd5TACUMvzGtN6SQQNXzLHkfm17MikviqBspLbGlD/pbw7xdby4DZ07Orx5 nkpLYw0= ---- END SSH2 PUBLIC KEY ----
Using the key on bulldog.unca.edu is a bit harder. I'm going to outline the procedure here and let those who are interested ask question. First, you need to create a directory called .ssh2 on bulldog.unca. and make sure that the directory cannot be read by anyone other than yourself. The easiest way to do this is to log into bulldog and then connect to candler.cs.unca.edu using ssh. This will create the right directories with the right rights.
bulldog% ssh candler.cs.unca.edu
Now you need to copy your public key into your .ssh2 directory. Let's say you call it CSCI173.pub. Now you must add a file called authorization to your .ssh directory that contains the line "key CSCI173.pub".
Now you must navigate to the Auth panel of PuTTY
and set the private file for SSH authentication
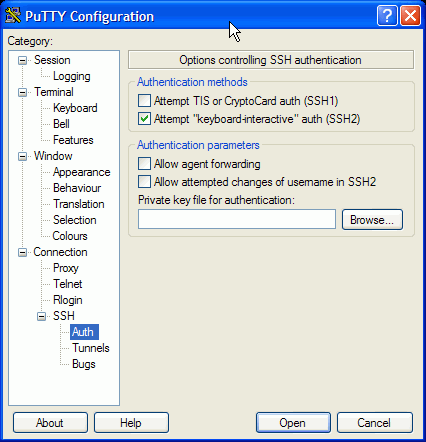
and then to the Connection panel to set the
Auto-login username
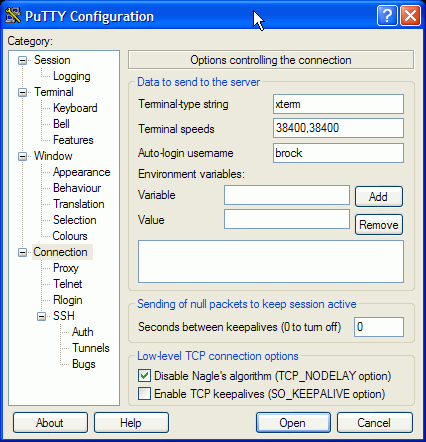
With luck you'll be able to connect without typing your bulldog password. However, you will have to type the private key passphrase, so you won't save much work.
gpg (GNU Privary Guard) is a patent-free encryption system that is similar to the very famous PGP (Pretty Good Privacy) system created by Philip Zimmermann.
To use gpg, you must first generate a public and private key. Do this with the gpg program. Here's an example of its use.
[yourid@machname yourid]$ gpg --gen-key
gpg (GnuPG) 1.2.1; Copyright (C) 2002 Free Software Foundation, Inc.
This program comes with ABSOLUTELY NO WARRANTY.
This is free software, and you are welcome to redistribute it
under certain conditions. See the file COPYING for details.
gpg: WARNING: using insecure memory!
gpg: please see http://www.gnupg.org/faq.html for more information
gpg: /home/brock/.gnupg: directory created
gpg: new configuration file `/home/brock/.gnupg/gpg.conf' created
gpg: keyblock resource `/home/brock/.gnupg/secring.gpg': file open error
gpg: keyring `/home/brock/.gnupg/pubring.gpg' created
Please select what kind of key you want:
(1) DSA and ElGamal (default)
(2) DSA (sign only)
(5) RSA (sign only)
Your selection? 1
DSA keypair will have 1024 bits.
About to generate a new ELG-E keypair.
minimum keysize is 768 bits
default keysize is 1024 bits
highest suggested keysize is 2048 bits
What keysize do you want? (1024)
Requested keysize is 1024 bits
Please specify how long the key should be valid.
0 = key does not expire
<n> = key expires in n days
<n>w = key expires in n weeks
<n>m = key expires in n months
<n>y = key expires in n years
Key is valid for? (0) 5y
Key expires at Mon 18 Jan 2010 10:13:51 PM EST
Is this correct (y/n)? y
You need a User-ID to identify your key; the software constructs the user id
from Real Name, Comment and Email Address in this form:
"Heinrich Heine (Der Dichter) <heinrichh@duesseldorf.de>"
Real name: J. Dean Brock
Email address: brock@cs.unca.edu
Comment:
You selected this USER-ID:
"J. Dean Brock <brock@cs.unca.edu>"
Change (N)ame, (C)omment, (E)mail or (O)kay/(Q)uit? o
You need a Passphrase to protect your secret key.
We need to generate a lot of random bytes. It is a good idea to perform
some other action (type on the keyboard, move the mouse, utilize the
disks) during the prime generation; this gives the random number
generator a better chance to gain enough entropy.
You might want to list your keys now.
[yourid@machname yourid]$ gpg --list-keys /home/brock/.gnupg/pubring.gpg ------------------------------ pub 1024D/B2086B06 2005-01-20 J. Dean Brock <brock@cs.unca.edu> sub 1024g/221A28F6 2005-01-20 [expires: 2010-01-19]
Now you must export your public key so that others may use it.
[yourid@machname yourid]$ gpg --output "PUBKEY.asc" --export --armor "J. Dean Brock <brock@cs.unca.edu>"
Go ahead and take a look at your key.
[yourid@machname yourid]$ cat PUBPGP.asc -----BEGIN PGP PUBLIC KEY BLOCK----- Version: GnuPG v1.2.1 (GNU/Linux) mQGiBEHvIqURBADeqPNIwI3s5zWgpTSx6p5Xz31PrcSGyJ212/sjxo1rQOK6TEkv PbOdB4nclCHUTjbLMWEAwH+PmVAxFryE2EHy+LaOkqESnsNW8u37ceOmizT57nd/ 5nZLYK/HccRsdazNWEPQH042v6knsIIuyY89XzEu6m76ySO1nplhmum77wCgy6LU 5gLFBN96fZg5SufykLJLsZMD/jZZS1SNff+tqpPdycPjUKiJNVFjkBU/o/hSb6Wj 44SQ4JUq33hfBVUlv0F5CS7HirTQUgYorgz9I3/vljvajb+jOLsG//+zKPF66hPk 7JsCxsRqIzo6XmOwysSzglMpQCgfH9JMHwExxfHKygZ99kIJTiWJhPYd44X+0n6b HgtIBADdBJCb5+TkDuJ1HhYfYVTpR8ExDrMqhLq3cOsc5554QSC+i3letC287qGR rZw/aDhgbVn3Bdp4WeJkJRGYM5eSovIp+r8WgXDkEzwnxxV7scJFZr2FUpGQ0xUD n2b65rDwvpbZPDRF2a+o1j4I106quf5pY0sexnaLZ5edEUjsLLQhSi4gRGVhbiBC cm9jayA8YnJvY2tAY3MudW5jYS5lZHU+iF8EExECAB8FAkHvIqUFCQlmAYAECwcD AgMVAgMDFgIBAh4BAheAAAoJEJozeEmyCGsGhrsAoKBU0CQR7e1WhnEh0AY/b1S6 E6ZZAJ9gVtpfoFQ6CHzx0zfoJOgNgwkJFbkBDQRB7yKmEAQAmhNHshcmnnwIifyi 7cSGE0OCB+9QLj4Hl+ZwhBTTkARR830NscWlUD3qRvE2ayqGqxyjsS2OcmQX8Ett bdEFhB+oTO4bcpaXudh99KEo3IeRMb95o2b4FuQ/hPnkjO+07x7Kr8ZBJ72OBvIK dyMrP7FdbP4boiAMZFU5/8Y33ksAAwUEAIVqCeEi3MBrD2Q3ATR/k7lqZ/mUUhbB a4zljZkUzkgXa/YtgMNrmD1PD5kBKG/kb95ITfKMq3ntJmRQ/T9VQ3ZISFb41G7W G3LenpHYT0ZC3dYY1agJAcAIadkisenRgygb9wNWnMSqCggtp5aKz/eNHQH0vJBl 0Rz7F90ofl+miEwEGBECAAwFAkHvIqYFCQlmAYAACgkQmjN4SbIIawaFCQCgl4Nq nflKj8iIA3mVWBzvMm9DFNwAoMbWJu6F9/WNYM+XCyMIgyHt0SUJ =U3kX -----END PGP PUBLIC KEY BLOCK-----
Now you want to import someone's public key into your key ring
[yourid@machname yourid]$ gpg --import ~anothercsci173student/PUBKEY.asc gpg: key EEC79E96: public key "CSCI 201 test <yourid@cs.unca.edu>" imported gpg: Total number processed: 1 gpg: imported: 1 [yourid@machname yourid]$ gpg --list-keys /home/brock/.gnupg/pubring.gpg ------------------------------ pub 1024D/B2086B06 2005-01-20 J. Dean Brock <brock@cs.unca.edu> sub 1024g/221A28F6 2005-01-20 [expires: 2010-01-19] pub 1024D/EEC79E96 2005-01-20 CSCI 201 test <yourid@cs.unca.edu> sub 1024g/193A046D 2005-01-20 [expires: 2010-01-19]
In the real world, you'd use your public and private keys to exchange important documents; but here's we'll just create a short and silly file. Type anything you wish between the double quotes to put your message within a file called secret.stuff.
[yourid@machname yourid]$ echo "Your secret message does here" > secret.stuff
Now you can encrypt and sign your message. The user id's that you enter are the folks to whom you are intending to send your message. Their public keys will be used in the ecryption of the message.
[yourid@candler .gnupg]$ gpg --armor --sign --encrypt ~/secret.stuff
You need a passphrase to unlock the secret key for
user: "CSCI 201 test <yourid@cs.unca.edu>"
1024-bit DSA key, ID EEC79E96, created 2005-01-20
Enter passphrase: csciisfun
You did not specify a user ID. (you may use "-r")
Enter the user ID. End with an empty line: brock
gpg: 221A28F6: There is no indication that this key really belongs to the owner
1024g/221A28F6 2005-01-20 "J. Dean Brock <brock@cs.unca.edu>"
Primary key fingerprint: 03AF 92AE 032C CD24 BDEA AAA7 9A33 7849 B208 6B06
Subkey fingerprint: 7179 D684 458F 8DCD 0DDB 3DBD C61C C3E7 221A 28F6
It is NOT certain that the key belongs to the person named
in the user ID. If you *really* know what you are doing,
you may answer the next question with yes
Use this key anyway? yes
Added 1024g/221A28F6 2005-01-20 "J. Dean Brock <brock@cs.unca.edu>"
Enter the user ID. End with an empty line:
[yourid@candler .gnupg]$
Now exchange your secret message with that of someone else.
[yourid@machname yourid]$ cp ~anothercsci173student/secret.stuff.asc secret.msg.asc
Now try to decrypt their secret message
[yourid@machname yourid]$ gpg --decrypt secret.stuff.asc
You need a passphrase to unlock the secret key for
user: "J. Dean Brock <brock@cs.unca.edu>"
1024-bit ELG-E key, ID 221A28F6, created 2005-01-20 (main key ID B2086B06)
gpg: encrypted with 1024-bit ELG-E key, ID 221A28F6, created 2005-01-20
"J. Dean Brock <brock@cs.unca.edu>"
This is so much fun
gpg: Signature made Wed 19 Jan 2005 10:36:39 PM EST using DSA key ID EEC79E96
gpg: Good signature from "CSCI 201 test >yourid@cs.unca.edu<"
gpg: checking the trustdb
gpg: checking at depth 0 signed=0 ot(-/q/n/m/f/u)=0/0/0/0/0/1
gpg: next trustdb check due at 2010-01-19
gpg: WARNING: This key is not certified with a trusted signature!
gpg: There is no indication that the signature belongs to the owner.
Primary key fingerprint: 0FB4 D58C A1DA 6A35 CF70 D853 A4E0 8555 EEC7 9E96
[yourid@machname yourid]$